In an era of sophisticated cyber threats and complex data ecosystems, a reactive security posture is no longer sufficient. The financial and reputational costs of a data breach are staggering, pushing businesses to adopt proactive defense mechanisms. But with countless options available, how do you build a security stack that actually works? This guide cuts through the noise. We'll explore 12 essential data breach prevention tools across six critical categories, from stopping accidental PII leaks in your analytics to locking down your cloud infrastructure.
This resource is designed for digital analysts, marketing teams, and developers who are responsible for data governance and privacy. We’ll analyze each tool's real-world use cases, strengths, and limitations, helping you choose the right combination to safeguard your most valuable asset: your data. Instead of generic marketing copy, you'll find an in-depth look at what makes each solution effective, with screenshots, direct links, and even video demonstrations to guide your evaluation.
Our goal is to help you move beyond basic compliance and build a resilient security framework that protects customer information and maintains trust. We will cover a range of solutions, including Data Loss Prevention (DLP), Security Information and Event Management (SIEM), and specialized analytics monitoring platforms like Trackingplan. As your organization strengthens its digital defenses, remember that a comprehensive data security strategy also involves physical device hygiene, such as understanding how to totally wipe an iPhone before selling it. This curated list will provide the insights you need to make informed decisions and proactively prevent data incidents before they occur.
1. Trackingplan
Best for: Automated analytics governance and PII leak detection.
Trackingplan stands out as a critical first line of defense in data breach prevention by focusing on the data that most organizations overlook: the customer data flowing from your websites and apps to third-party analytics and marketing tools. It operates as an always-on observability platform, automating the entire process of discovering, monitoring, and validating your analytics implementation. This proactive approach ensures data integrity and, crucially, prevents sensitive information like personally identifiable information (PII) from being accidentally collected or sent to unauthorized destinations.
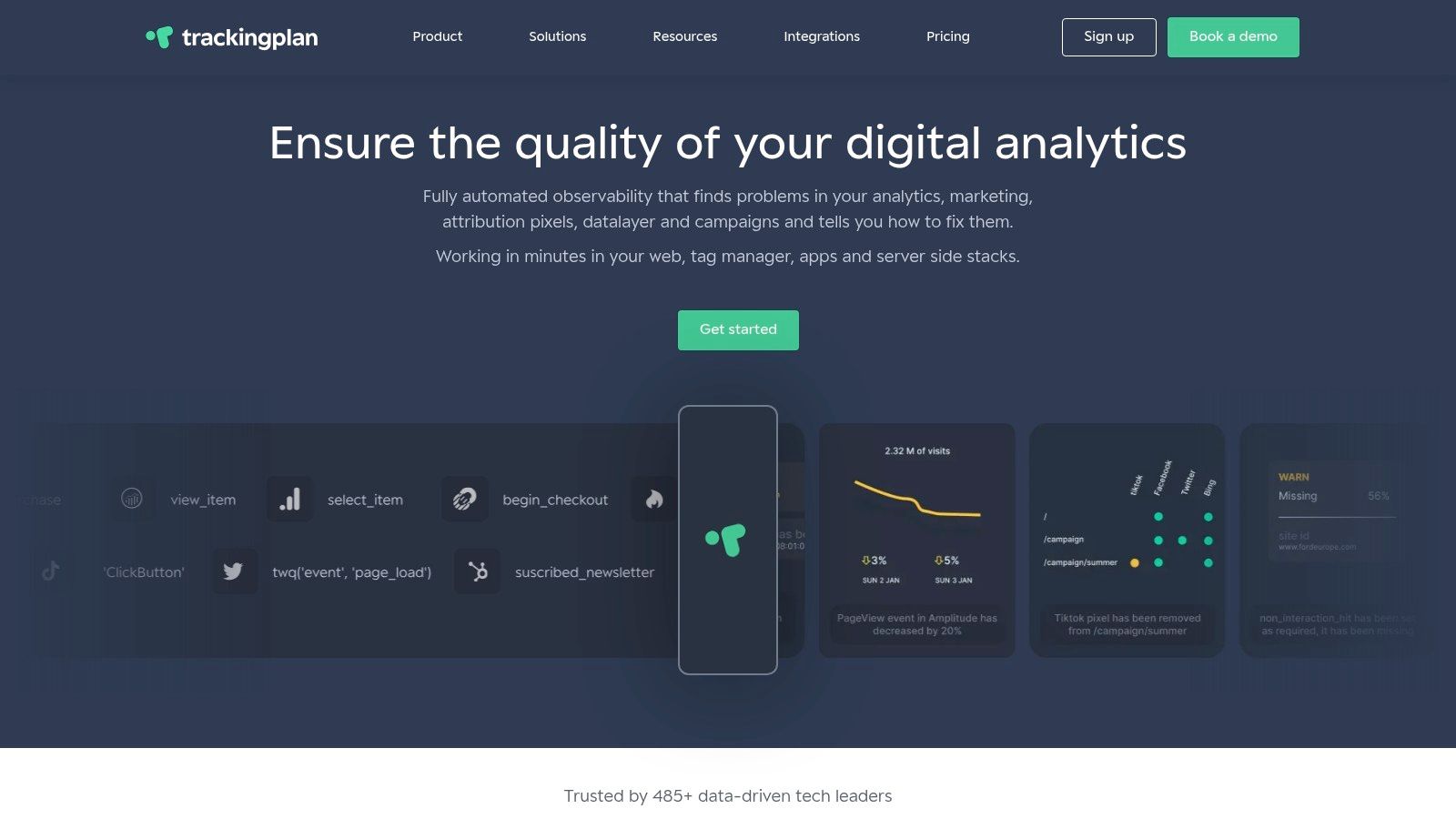
Unlike traditional security tools that focus on network perimeters or server vulnerabilities, Trackingplan targets the data layer itself. It automatically builds and maintains a comprehensive tracking plan, essentially a real-time inventory of all your data points and where they are going. This automated discovery eliminates the need for manual audits, which are often outdated the moment they are completed. By continuously monitoring every event, it instantly detects anomalies that could signal a data breach in the making.
Key Strengths & Use Cases
- PII & Sensitive Data Leak Detection: Configure custom rules to automatically scan for and alert on patterns matching sensitive data (like emails, credit card numbers, or social security numbers) in your analytics payloads. This is a powerful feature for GDPR, CCPA, and HIPAA compliance.
- Rogue and Unapproved Tracking: Receive instant alerts when new, unapproved tracking pixels or data destinations appear on your site. This helps shut down potential data exfiltration points introduced by third-party scripts or misconfigurations.
- AI-Assisted Root Cause Analysis: When an issue is detected, Trackingplan doesn't just send an alert. Its AI-powered engine details precisely where the problem occurred in the code, why it happened, and provides actionable steps to fix it, significantly reducing Mean Time to Resolution (MTTR).
- Supply Chain Security: Gain visibility into the data collection practices of third-party vendors and pixels integrated into your digital properties, ensuring they adhere to your data governance policies.
Implementation and User Experience
Onboarding is remarkably straightforward and designed for minimal engineering effort. Installation involves adding a lightweight (~10 KB) JavaScript tag or a small SDK that loads asynchronously, ensuring no impact on site performance or user experience. The platform automatically begins mapping your data flows, with high-traffic sites seeing a complete picture within hours. The interface is clean and built for collaboration between technical and non-technical teams, including marketers, analysts, and developers.
Limitations to Consider
- Pricing: Enterprise and agency pricing is not publicly listed on the website; you will need to engage with their sales team for a custom quote based on your traffic and needs.
- Initial Discovery Time: While fast for most, very low-traffic websites or specific development environments might take longer (up to a week) to fully populate the initial data map.
- Alert Configuration: The system is powerful, but you may need to spend some initial time fine-tuning validation rules and alert thresholds to match your specific business logic and avoid noise.
Website: https://trackingplan.com
2. Microsoft Purview Data Loss Prevention
For organizations deeply integrated into the Microsoft 365 ecosystem, Microsoft Purview Data Loss Prevention offers a powerful, natively integrated solution. It stands out by providing a unified, cloud-managed console to create and enforce DLP policies across a wide range of Microsoft services, including Teams, Exchange, SharePoint, and OneDrive, as well as on-premises files and endpoints. This makes it one of the most cohesive data breach prevention tools for businesses already leveraging Microsoft's suite.
Its primary strength is its seamless integration and rapid time-to-value for existing M365 tenants. Purview uses built-in and custom classifiers, including adaptive machine learning, to automatically identify sensitive information like financial data or PII. Policies can then block sharing, encrypt data, or alert administrators when risky behavior is detected, providing a proactive defense mechanism. Recent updates extend these controls to AI applications and third-party AI agents, addressing modern data exfiltration vectors.
Key Insight: The true value of Purview DLP is realized when it is used as a central nervous system for data governance within a Microsoft-centric environment, unifying policy management from the cloud to the endpoint.
Core Use Cases & Implementation
- Protecting M365 Data: Enforce policies to prevent sensitive data from being shared externally via Teams chats, SharePoint sites, or Exchange emails.
- Endpoint DLP: Monitor and control user actions on Windows devices, such as copying sensitive files to USB drives or personal cloud storage.
- AI Governance: Apply DLP policies to interactions with Microsoft Copilot and other AI agents to prevent sensitive data from being used in prompts.
Implementation requires specific Microsoft 365 licensing, typically E5/A5/G5, or standalone compliance SKUs. While the initial setup can be complex, the unified Purview console simplifies ongoing management. For a broader understanding of how DLP fits into a complete strategy, you can explore more about preventing data loss and its core principles.
3. Google Cloud Sensitive Data Protection (DLP)
For organizations building their data infrastructure on Google Cloud Platform (GCP), Sensitive Data Protection offers a powerful, API-driven service for discovering, classifying, and protecting sensitive data at scale. Rather than a policy-enforcement tool like traditional DLP, it functions as a data intelligence engine. It excels at scanning massive datasets in BigQuery, Cloud Storage, and Cloud SQL to identify and profile sensitive information, making it one of the most effective data breach prevention tools for cloud-native environments.
Its primary strength lies in its programmatic approach and deep integration with GCP. With over 100 built-in detectors, it can automatically find PII, financial data, and credentials. Developers can then use its APIs to de-identify data through redaction, masking, or tokenization before it's used in analytics or development workflows. This shifts protection from blocking transfers to making data safe by default.
Key Insight: Google's DLP is best viewed as a foundational data security service for GCP, enabling teams to build automated discovery and de-identification pipelines rather than just enforcing rules at the perimeter.
Core Use Cases & Implementation
- Data Discovery & Classification: Run large-scale profiling jobs on BigQuery tables or Cloud Storage buckets to create a comprehensive inventory of where sensitive data resides.
- Automated De-Identification: Integrate its APIs into data processing pipelines (e.g., Cloud Functions, Dataflow) to automatically redact or tokenize PII in real time.
- Hybrid Data Scanning: Use hybrid jobs to scan data in on-premises databases or other clouds, extending discovery beyond the GCP ecosystem.
Implementation is API- and console-driven, operating on a pay-as-you-go model with a generous free tier for inspection and profiling. While this transparency is a plus, costs can escalate with very large or frequent scans if not configured carefully. Understanding best practices for ensuring PII data compliance is key to maximizing its value.
4. Amazon Macie
For organizations operating within the Amazon Web Services (AWS) ecosystem, Amazon Macie is an essential, fully managed data security service. It excels at discovering, classifying, and protecting sensitive data stored in Amazon S3. By using machine learning and pattern matching, Macie continuously evaluates S3 buckets to identify and alert on potential risks, such as publicly accessible buckets or the presence of Personally Identifiable Information (PII), making it a cornerstone among data breach prevention tools for cloud-native companies.
Its primary advantage lies in its seamless, native integration with AWS. Enabling Macie across an organization's accounts is straightforward, providing immediate visibility into data security posture within S3. It automatically generates an inventory of S3 buckets and evaluates their access controls and encryption policies. This proactive monitoring helps teams quickly identify and remediate data exposure risks before they can be exploited, directly addressing a common vector for data breaches.
Key Insight: Macie's strength is its laser focus on S3, the de facto object storage for modern applications. It turns what can be a sprawling and opaque data landscape into a managed and observable security asset.
Core Use Cases & Implementation
- S3 Data Discovery: Continuously scan S3 buckets to locate and classify sensitive data like credentials, financial information, and PII.
- Security Posture Monitoring: Monitor S3 buckets for security weaknesses, such as unencrypted storage or public accessibility, and receive alerts.
- Compliance & Auditing: Generate findings that provide evidence for compliance frameworks by demonstrating that sensitive data is properly identified and secured.
Implementation involves enabling the service in the AWS Management Console. Macie offers a 30-day free trial for automated data discovery and bucket-level evaluation. While the service is easy to activate, organizations should be mindful of potential S3 request costs incurred during deep scans of large data sets.
- Website: Amazon Macie
5. AWS Marketplace
For organizations operating within the Amazon Web Services ecosystem, the AWS Marketplace serves as a powerful procurement hub rather than a standalone tool. It simplifies sourcing and deploying a wide range of third-party data breach prevention tools, from advanced Data Security Posture Management (DSPM) solutions to traditional DLP and insider risk management platforms. The platform streamlines the entire procurement lifecycle, from discovery and security vetting to billing and deployment.
Its core value is its deep integration with AWS accounts, allowing for consolidated billing and the ability to apply purchases toward Enterprise Discount Program (EDP) commitments. Features like AWS Vendor Insights provide pre-vetted security and compliance information, significantly reducing the time required for internal legal and security reviews. This allows teams to acquire and implement critical security software much faster than through traditional channels.
Key Insight: AWS Marketplace is not a tool itself, but a strategic accelerator for acquiring, vetting, and managing a portfolio of security tools, enabling organizations to leverage their existing AWS relationship to enhance their security posture efficiently.
Core Use Cases & Implementation
- Streamlined Procurement: Quickly purchase and deploy security tools like DLP or DSPM solutions using pre-negotiated terms or private offers.
- Security Vetting Acceleration: Use Vendor Insights to access security and compliance attestations, speeding up internal vendor risk assessments.
- Budget Optimization: Consolidate software spend onto your AWS bill and count it toward enterprise discount commitments.
Implementation involves searching the marketplace for desired software categories, evaluating listings, and subscribing through an AWS account. While the platform simplifies acquisition, the configuration of each purchased tool remains a separate process. Understanding how different tools fit together is crucial for a complete data governance strategy.
- Website: AWS Marketplace
6. Netskope One – Data Loss Prevention
Netskope One offers a cloud-native Security Service Edge (SSE) platform, providing advanced Data Loss Prevention capabilities that extend far beyond traditional perimeters. It excels at enforcing unified policies across cloud services (SaaS/IaaS), web traffic, email, private applications, and endpoints. This unified approach makes it a standout choice among data breach prevention tools for enterprises seeking consistent visibility and control over data in motion and at rest, regardless of user location.
Its primary strength is its ability to inspect traffic from any source to any destination through a single-pass architecture. Netskope uses a vast library of pre-built and custom classifiers to identify sensitive data like PII, PCI, and intellectual property. Administrators can then apply granular controls, such as blocking uploads to unsanctioned cloud apps, preventing copy/paste of sensitive information, or quarantining files shared improperly, all from a centralized policy engine.
Key Insight: Netskope One’s real power lies in its deep context-awareness, allowing it to enforce zero-trust principles for data protection across hybrid work environments where data flows between managed and unmanaged applications.
Core Use Cases & Implementation
- Cloud & Web Security: Prevent sensitive data exfiltration through shadow IT, unsanctioned web services, or high-risk SaaS applications.
- Granular Activity Control: Enforce policies based on user, group, device, location, and activity (e.g., allow "view" but block "download" in a specific app).
- Data Discovery: Scan and classify sensitive data at rest in sanctioned cloud storage services like Google Workspace or Microsoft 365.
Implementation is an enterprise-level endeavor that requires careful planning and tuning to maximize its effectiveness. Pricing is quote-based and tailored to organizational needs. The platform's comprehensive scope provides powerful protection but demands a dedicated effort for initial deployment and ongoing policy management.
- Website: Netskope Data Loss Prevention
7. Proofpoint Enterprise DLP
With a strong heritage in email security, Proofpoint Enterprise DLP offers a human-centric approach to data protection. It extends its mature security capabilities from email to cloud applications and endpoints, providing a unified console for managing incidents across all channels. This makes it a compelling choice among data breach prevention tools for organizations looking to correlate user behavior with data movement, especially in threat-heavy environments like email.
The solution's core strength lies in its ability to connect data loss events to user actions and potential threats, using behavioral analytics to provide context for investigations. Its lightweight endpoint agent and privacy-by-design controls ensure comprehensive monitoring without compromising user privacy. For businesses needing to meet data residency requirements, Proofpoint also offers regional data centers, a crucial feature for global compliance.
Key Insight: Proofpoint's human-centric focus transforms DLP from a simple content-aware tool into an investigative platform, linking data loss incidents directly to user risk and behavior.
Core Use Cases & Implementation
- Email & Cloud Security: Prevent sensitive data exfiltration through corporate email or unauthorized cloud services like personal Dropbox or Google Drive accounts.
- Insider Risk Investigation: Use behavioral analytics and user timelines to investigate incidents, distinguishing between accidental exposure and malicious intent.
- Endpoint Data Control: Monitor and block sensitive data from being copied to USB devices, printed, or transferred via unsanctioned applications on user workstations.
Implementation is geared toward enterprise environments, often with the support of Proofpoint's professional services to help operationalize the program. It integrates with SIEM and SOAR platforms to streamline incident response workflows. Pricing is quote-based and tailored to organizational needs.
- Website: Proofpoint Enterprise DLP
8. CrowdStrike Falcon Data Protection
For organizations already leveraging the CrowdStrike Falcon platform for endpoint detection and response (EDR), the Falcon Data Protection module offers a highly efficient, integrated approach to preventing data exfiltration. It extends the existing single-agent architecture to monitor and control how sensitive data moves on endpoints and to web destinations. This makes it one of the most operationally simple data breach prevention tools for existing CrowdStrike customers seeking to consolidate their security stack.
Its core advantage lies in its unified agent and console, which eliminates the need to deploy and manage a separate DLP solution. Falcon Data Protection leverages the platform's deep endpoint telemetry to provide context-rich visibility into data egress paths, monitoring file uploads, sharing activities, and clipboard usage in real-time. Policies can be configured to block or monitor actions based on file classification, destination, or user context, directly from the familiar Falcon console.
Key Insight: The primary value of Falcon Data Protection is its seamless operational integration. It adds critical data loss prevention capabilities without increasing agent bloat or management complexity for security teams already invested in the Falcon ecosystem.
Core Use Cases & Implementation
- Insider Risk Mitigation: Monitor and control data movement on employee endpoints to prevent accidental leaks or malicious exfiltration to unauthorized USB drives or cloud services.
- Unified Endpoint Control: Enforce both device control (e.g., block USBs) and data-aware policies through the same agent used for EDR and antivirus.
- Contextual Investigations: Use the rich telemetry from the Falcon platform to investigate data loss incidents alongside other security events like malware infections or identity threats.
Implementation requires an existing CrowdStrike Falcon subscription, as the Data Protection module is a separately licensed add-on. The setup is streamlined for current customers, with policies configured within the central Falcon UI. This unified approach provides a powerful combination of threat detection and data protection. To see how visibility into data flows is crucial, watch Trackingplan's video on detecting data leaks, which highlights similar principles of monitoring.
- Website: CrowdStrike Falcon Data Protection
9. Fortra Digital Guardian
Fortra’s Digital Guardian is an enterprise-grade Data Loss Prevention (DLP) platform renowned for its deep endpoint visibility and granular control over data movement. It provides a comprehensive suite that covers endpoint, network, and cloud environments, allowing organizations to apply unified policies across their entire data landscape. This focus on endpoint control and intellectual property (IP) protection makes it one of the most robust data breach prevention tools for industries where sensitive R&D or trade secrets are paramount.
The platform excels at data discovery and classification, using its Analytics & Reporting Cloud (ARC) to provide rich context around data usage and user behavior. This allows security teams to move beyond simple rule-based blocking and understand the intent behind data actions, significantly reducing false positives. For organizations needing additional support, Fortra also offers managed services, offloading the complexity of policy tuning and incident response.
Key Insight: Digital Guardian’s core strength is its agent-based, context-aware endpoint protection that can enforce highly specific controls, such as blocking copy-paste actions or printing of sensitive files, regardless of user location.
Core Use Cases & Implementation
- Intellectual Property Protection: Prevent the exfiltration of trade secrets, design documents, and source code from endpoints via USB, cloud apps, or email.
- Insider Risk Management: Monitor and analyze user behavior to detect anomalous activity that could indicate an impending data breach or a malicious insider.
- Regulatory Compliance: Discover, classify, and protect PII, PHI, and financial data to meet GDPR, CCPA, and HIPAA requirements across the hybrid enterprise.
Implementation can be complex, especially in large environments, often benefiting from professional services for initial deployment and policy configuration. The platform is available as a SaaS or on-premises solution, offering flexibility. Pricing is quote-based and tailored to the specific needs of the organization.
- Website: Fortra Digital Guardian
10. Code42 Incydr
Code42 Incydr shifts the focus from traditional broad-based DLP to a specialized insider risk management (IRM) solution. It is laser-focused on detecting and responding to data exfiltration from endpoints, cloud services, and email. Incydr excels at monitoring file movements to untrusted locations like personal cloud storage, removable media, or web browsers, making it a critical tool for organizations concerned about employees (whether malicious or negligent) taking sensitive data with them.
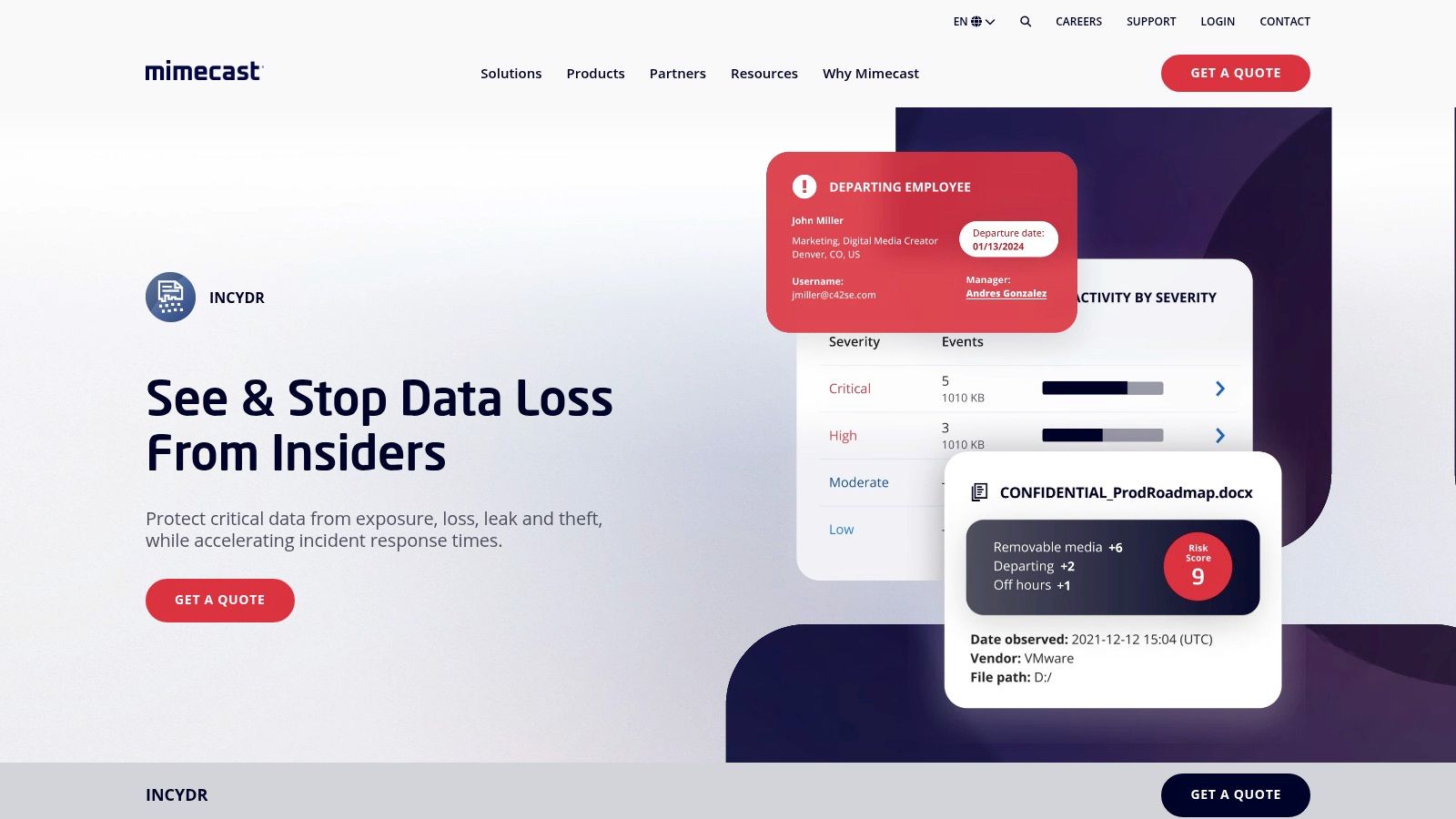
Its strength lies in its rapid time-to-value and "policy-lite" approach, which prioritizes signal over noise. Instead of complex rule creation, Incydr provides context on who is moving what data, where, and when, allowing security teams to quickly triage potential threats. This makes it one of the more agile data breach prevention tools for combating the specific threat of insider-driven data loss across Windows, macOS, and Linux endpoints.
Key Insight: Incydr is not a general-purpose DLP; it is a purpose-built exfiltration detection and response platform that provides high-fidelity alerts on data movement, enabling security teams to act decisively on insider risks.
Core Use Cases & Implementation
- Insider Risk Triage: Quickly identify and investigate high-risk file activity associated with departing employees or suspicious user behavior.
- Cloud & Email Monitoring: Use API integrations to monitor file sharing and exfiltration from corporate OneDrive, Google Drive, Box, and email systems.
- Data Exposure Visibility: Gain a clear view of how files are leaving the corporate environment via browsers, Airdrop, USB drives, and other vectors.
Implementation involves deploying a lightweight agent to endpoints and connecting to cloud services via APIs. Pricing is enterprise-focused and typically provided through sales channels or private offers on the AWS Marketplace. The platform also offers a FedRAMP-authorized version for government clients, highlighting its security credentials.
- Website: Code42 Incydr
11. Varonis Data Security Platform
Varonis takes a data-centric approach to security, focusing on protecting sensitive information wherever it lives, from on-premises file servers to SaaS applications like Microsoft 365 and Salesforce. It excels at answering critical data security questions: where is my sensitive data, who can access it, and is that access being used appropriately? This makes it one of the most comprehensive data breach prevention tools for organizations looking to lock down unstructured and semi-structured data stores.
The platform’s strength lies in its automated risk remediation. Varonis not only discovers and classifies data but also maps permissions and analyzes activity to pinpoint risks like excessive access or stale data. It then automates the process of revoking unnecessary permissions and locking down sensitive files, drastically reducing the attack surface. Its behavioral analytics engine builds a baseline of normal user activity and flags deviations, providing early warnings of potential threats like ransomware or insider attacks.
Key Insight: Varonis provides a crucial layer of visibility and automated control over data itself, complementing network and endpoint security by focusing on the ultimate target of any breach.
Core Use Cases & Implementation
- Automated Data Discovery & Classification: Continuously scan and classify sensitive data (PII, PCI, PHI) across on-prem, cloud, and SaaS environments.
- Access Governance & Remediation: Identify and automatically fix over-permissioning, global access groups, and broken inheritance to enforce a least-privilege model.
- Threat Detection & Response: Detect anomalous user behavior, ransomware patterns, and insider threats with detailed forensic logs for investigation.
Implementation is a significant enterprise project requiring careful planning and tuning, as the platform needs to integrate with various data stores. Pricing is quote-based and tailored to the organization's specific environment, requiring engagement with the Varonis sales team via a demo.
- Website: Varonis Data Security Platform
12. BigID
As a leader in Data Security Posture Management (DSPM), BigID provides an AI-augmented platform designed to discover, manage, and protect sensitive data across complex hybrid and multi-cloud environments. It specializes in providing deep visibility into what and where your critical data is, who has access to it, and how it’s being used. This makes it one of the most foundational data breach prevention tools for organizations struggling with data sprawl and shadow data.
BigID’s core strength is its agentless, deep data discovery and classification engine that can scan structured, unstructured, and semi-structured data sources. The platform moves beyond simple pattern matching, using machine learning to identify context and relationships within data. This enables powerful risk remediation actions like automated data labeling, masking, redaction, and deletion, directly addressing the root causes of potential breaches. Its Cloud DLP capabilities extend these controls to services like Amazon S3 and OneDrive.
Key Insight: BigID excels at creating a unified inventory of all enterprise data, providing the foundational visibility required for security, privacy, and governance teams to collaborate on risk reduction and compliance.
Core Use Cases & Implementation
- Data Discovery & Classification: Automatically scan and classify sensitive data (PII, PCI, PHI) across on-premises databases, cloud storage, and SaaS applications.
- Risk Remediation: Identify and remediate data risks such as overexposed permissions, duplicate sensitive files, or non-compliant data retention.
- Cloud Data Security: Apply Data Activity Monitoring and Cloud DLP policies to monitor and control how data is used and shared in cloud environments like S3 and SharePoint.
Implementation involves deploying connectors for your various data sources. While the platform is powerful, successful deployment often requires coordination between security, privacy, and data governance teams. Pricing is customized based on the number of connectors and deployment scale.
- Website: BigID
Top 12 Data Breach Prevention Tools Comparison
Building Your Proactive Defense: The Final Takeaway
Navigating the landscape of data breach prevention tools can feel overwhelming, but the journey from vulnerability to resilience begins with a single, strategic step: visibility. Throughout this guide, we've explored a diverse arsenal of solutions, from enterprise-wide DLP platforms like Microsoft Purview and Proofpoint to cloud-native guardians like Amazon Macie and Google Cloud DLP. Each tool offers a powerful piece of the data security puzzle.
However, the most critical takeaway is that a truly effective defense is not a single product but a layered, interconnected ecosystem. Your security posture is only as strong as its weakest link, and for modern digital businesses, that vulnerability often lies in the blind spots of your client-side data collection. This is where your marketing pixels, analytics tags, and third-party integrations continuously transmit user information, creating a dynamic and often unmonitored attack surface.
Shifting from a Reactive to a Proactive Mindset
The traditional approach to data security has been reactive, focusing on building walls and responding to alarms after a breach has occurred. The modern imperative, however, is to be proactive. This means shifting your focus from simply blocking threats to deeply understanding your data's entire lifecycle.
A proactive strategy involves:
- Continuous Monitoring: You cannot protect what you cannot see. Gaining real-time visibility into every data point, especially PII being collected and sent from your websites and apps, is the foundational layer.
- Automated Validation: Manually checking thousands of data points and consent configurations is impossible. Automation is essential to validate that your data collection aligns perfectly with your privacy policies and user consent choices.
- Cross-Functional Collaboration: Data security is a team sport. Your marketing, analytics, and development teams must have shared visibility and accountability to prevent misconfigurations that lead to data leaks.
Choosing Your Stack: A Tailored Approach
There is no one-size-fits-all combination of data breach prevention tools. Your ideal security stack depends on your specific operational environment, risk profile, and regulatory obligations.
Consider these factors when building your defense:
- For Analytics & Marketing Stacks: Start with a specialized analytics monitoring tool like Trackingplan. It provides the essential first line of defense by detecting PII leaks, consent violations, and data misconfigurations right at the source, before sensitive data even reaches your servers or third-party vendors.
- For Cloud-Centric Organizations: Augment your defenses with cloud-native tools like AWS Macie or Google Cloud DLP. These are designed to discover and classify sensitive data within your cloud storage and databases, integrating seamlessly with your existing cloud infrastructure.
- For Large Enterprises: Layer on a comprehensive DLP solution like Netskope or Proofpoint. These platforms provide robust policy enforcement across endpoints, networks, and the cloud, helping you control data exfiltration and enforce corporate governance at scale.
Ultimately, the goal is to create a multi-layered shield where each tool complements the others. By combining the client-side, real-time alerting of a solution like Trackingplan with the broader data-at-rest and data-in-transit protection of traditional DLP and cloud security tools, you build a resilient and proactive security posture. This integrated approach doesn't just prevent breaches; it builds trust with your users and safeguards your brand's reputation in an increasingly data-conscious world.
Ready to close the biggest blind spot in your data security strategy? See how Trackingplan provides the essential first layer of defense by automatically detecting PII leaks and consent violations in your analytics and marketing tags. Sign up for free and start securing your client-side data today.









