A data processing agreement (DPA) is a legally binding contract between a data controller (that's you) and a data processor (like a vendor or service provider). Think of it as the official rulebook that clearly defines how a third party—say, your analytics platform or marketing automation tool—is allowed to handle your users' data. In short, it's an absolute must-have for data privacy compliance.
Understanding the Data Processing Agreement

At its heart, a DPA is a critical safeguard. When your company collects personal information from users—whether it’s an email for a newsletter or behavioral data for analytics—you become the data controller. This title comes with a heavy weight: you are legally on the hook for protecting that information.
But let's be realistic, you rarely handle all that data yourself. You rely on an ecosystem of third-party services, or data processors, for everything from sending marketing emails with Mailchimp to analyzing user behavior with Google Analytics.
A DPA contractually binds these vendors to handle that data according to your specific instructions and, more importantly, the law. Without one, you're essentially handing over sensitive user data and just hoping for the best, creating a massive blind spot and a huge risk for your business.
Why Is a DPA Non-Negotiable?
A solid Data Processing Agreement isn't just good business hygiene; it's a legal requirement under a growing number of privacy regulations. Since the EU's groundbreaking General Data Protection Regulation (GDPR) came into force on May 25, 2018, DPAs have become a cornerstone of global data governance.
It's not just a European thing, either. A staggering 71% of countries now have data privacy laws in place. And they have teeth. GDPR violations can trigger fines up to €20 million or 4% of global annual turnover, a stark reminder of why these agreements are so vital. If you want to dig deeper, you can explore more GDPR statistics to see its worldwide impact.
This makes the DPA essential for several key reasons:
- Legal Compliance: It satisfies a core requirement of laws like GDPR and CCPA, shielding your business from potentially crippling fines.
- Risk Mitigation: It legally binds your vendors to specific security and confidentiality standards, dramatically reducing the risk of a data breach caused by a third party's mistake.
- Building Trust: It shows your customers that you take their privacy seriously. In an age of data skepticism, that's a powerful way to build brand loyalty.
A Data Processing Agreement isn't just a legal formality; it's a foundational pillar of modern data strategy. It translates abstract privacy principles into concrete, enforceable actions that protect your company, your partners, and most importantly, your users.
Defining Roles and Responsibilities
One of the most important jobs of a DPA is to clearly spell out the roles of the data controller and the data processor. This clarity isn't just for show—each role carries distinct legal obligations. The controller is the one who determines the "why" and "how" of data processing, while the processor simply acts on the controller's documented instructions.
To help clear this up, here's a quick breakdown:
Controller vs Processor At a Glance
Think of it this way: if you run an e-commerce store, you are the data controller. You decide to collect customer shipping addresses for the express purpose of fulfilling orders. The third-party shipping software you use is the data processor; its only job is to handle those addresses to print labels exactly as you've instructed.
The DPA is what ensures the shipping company can't turn around and use those addresses for its own marketing or, worse, sell them. This clear division of responsibility, formalized in a DPA, is the key to managing data ethically and compliantly across your entire tech stack.
How Global Privacy Laws Shape Your DPA Requirements
While GDPR set the modern standard for data privacy, the need for a Data Processing Agreement is no longer just a European problem. We're seeing a "GDPR effect" ripple across the globe, with similar regulations popping up everywhere. This has turned the DPA into a universal tool for compliance.
Think of GDPR as the original blueprint for a house. Since it was built, countries and states worldwide have used it as a model, each adding their own local flair. This has created a complex patchwork of rules, but the DPA remains the common thread—the foundational contract that connects them all.
This global puzzle requires a consistent approach to data handling. A solid DPA helps you manage your obligations across this intricate legal map without having to reinvent the wheel every time you enter a new market.
The Growing Influence of US State Privacy Laws
In the United States, the absence of a federal privacy law has led to a fascinating and complex situation where individual states are taking the lead. California was the trailblazer with the California Consumer Privacy Act (CCPA), which, much like GDPR, imposes strict rules and requires DPA-like contracts with service providers.
Following California's lead, a wave of other states has jumped in:
- Colorado Privacy Act (CPA): This law gives consumers rights that will feel very familiar to anyone who's worked with GDPR or CCPA, requiring clear agreements with third-party processors.
- Virginia Consumer Data Protection Act (CDPA): Much like its counterparts, the VCDPA mandates strong contracts between controllers and processors to govern data activities.
- Utah Consumer Privacy Act (UCPA): Another one for the list, this act requires formal agreements to ensure vendors are properly protecting consumer data.
The explosion of state-level privacy laws has turned DPAs into mission-critical documents for data teams. As of 2023, multiple US states have rolled out tough regulations that mirror GDPR's spirit. Globally, the numbers are even more stark: 61% of countries (not including the EU) now have their own data protection rules.
China's Cyberspace Administration even issued its own Standard Contract for Cross-Border Transfers on February 24, 2023. These rules require explicit consent and impact assessments for high-risk processing, showing clear alignment with GDPR's standards.
The takeaway is clear: if your business operates across the US, you can't afford to wing it. Managing vendor relationships without a one-size-fits-all DPA strategy is a surefire way to risk non-compliance in a legal environment that's changing by the day. To avoid costly mistakes, it's wise to learn how to prevent privacy fines under CCPA and GDPR.
A Look at Other International Frameworks
This trend extends far beyond Europe and the United States. Many countries have either updated their old laws or introduced entirely new ones that echo the principles of GDPR, making the DPA a globally recognized instrument.
For instance, Switzerland beefed up its Federal Act on Data Protection (FADP) to align more closely with GDPR, reinforcing the need for clear contractual obligations. Similarly, countries from Brazil (with its LGPD) to Japan (APPI) have strengthened their privacy frameworks.
These foundational principles are often reflected in a company's public-facing policies. Understanding how global laws influence creating a robust Privacy Policy can give you deeper insight into what's expected from your DPAs.
Ultimately, it doesn't matter where your users are. The expectation is the same everywhere: their data must be protected through clear, legally-binding agreements.
Deconstructing the Core Clauses of a Data Processing Agreement

Let's be honest: diving into a data process agreement can feel like trying to read a foreign language. The dense legal text is intimidating, but its core components are surprisingly straightforward once you know what to look for. Think of this section as your translation guide, turning complex legalese into a practical checklist.
By understanding these essential clauses, you can review any vendor DPA with confidence, spotting both good terms and potential red flags. These clauses are the non-negotiable heart of the agreement, ensuring your data stays protected and your business stays compliant.
Remember, a DPA is a binding legal document. To fully grasp its power, it's helpful to understand the fundamental principles of breach of contract. If a vendor fails to uphold their end of the deal, there are serious consequences.
The Scope of Processing
The first and most critical clause defines the scope of processing. This is the "who, what, when, where, and why" of your data. It must explicitly state the subject matter, duration, nature, and purpose of the processing activities.
A solid scope clause should clearly list:
- Categories of data subjects: Who does the data belong to? Think website visitors, app users, or paying customers.
- Types of personal data: What specific information is being handled? This could be anything from email addresses and IP addresses to user IDs and purchase history.
- Purpose of processing: Why does the vendor need this data? Examples include sending marketing emails, analyzing product usage, or processing payments.
Be wary of vague or overly broad language. If a vendor’s DPA allows them to process "any data for business improvement," that’s a major red flag. A good clause is precise, ensuring the vendor can only use your data for the exact services you hired them for—nothing more.
Security Measures and Confidentiality
This clause is the DPA’s security blueprint. It contractually obligates your vendor to implement and maintain specific technical and organizational security measures. This isn't just a pinky promise; it’s a legally binding commitment to protect your data.
Look for explicit mentions of security practices, such as:
- Encryption: Covering data both in transit (moving across networks) and at rest (stored on servers).
- Access Controls: Procedures to ensure only authorized personnel can access data, often including role-based permissions and multi-factor authentication.
- Confidentiality Agreements: A requirement that all employees handling the data are bound by strict confidentiality obligations.
A weak clause might just say the vendor will use "reasonable security measures." A strong one will reference specific security standards (like ISO 27001) or detail the exact controls they have in place.
This is where the DPA transitions from a legal document to an operational one. It forces a clear conversation about security expectations, ensuring both parties are aligned on what it takes to keep data safe from unauthorized access or breaches.
Rules for Sub-Processors
Your vendor rarely works alone. They often use other companies—known as sub-processors—for essential services like cloud hosting (Amazon Web Services) or customer support (Zendesk). This clause governs how that's allowed to happen, giving you visibility and control over the entire data chain.
A robust sub-processor clause will require your vendor to:
- Obtain Prior Written Consent: They can’t just hire a new sub-processor without your specific authorization.
- Maintain a List: The vendor must keep an up-to-date list of all sub-processors handling your data.
- Impose a Back-to-Back DPA: They must have a DPA with each sub-processor that offers at least the same level of data protection as your agreement with them.
This prevents a nightmare scenario where your carefully vetted, secure vendor passes your data to an unknown, insecure third party. You're still on the hook for what happens down the chain, so this control is absolutely critical.
Data Breach Notification and Assistance
If a data breach happens on the vendor's end, this clause dictates what happens next. Speed and clarity are everything. The DPA must require the processor to notify you of a breach "without undue delay." Some of the best agreements will even specify a hard timeframe, like within 24 or 48 hours.
The clause should also outline the vendor's duty to help you respond. This means providing all the necessary information about the breach so you can fulfill your legal obligations to notify regulatory authorities and affected individuals. A red flag would be any language that dilutes this responsibility or creates vague timelines.
Audit Rights and Data Deletion
Finally, a strong DPA ensures accountability through audit rights and defines a clear end-of-life for your data. The audit clause gives you the right to verify that the processor is actually doing what they promised in the DPA. This might involve questionnaires, security certifications, or even on-site inspections.
The data deletion clause specifies what happens when your contract ends. It should give you the choice to have all personal data either returned to you or securely deleted from their systems. This simple clause prevents vendors from retaining your data indefinitely, closing a massive privacy loop. Without it, your users' data could sit on a vendor's servers long after you've stopped using their service.
To help you quickly identify what matters most, here’s a checklist summarizing the essential clauses you should find in any DPA. Use it to vet vendor contracts and spot potential issues before you sign.
Essential DPA Clauses Checklist
Having this checklist handy ensures you never overlook a critical protection. A vendor who pushes back on these fundamental points might not be the right partner for handling your valuable data.
How to Implement DPAs Across Your Tech Stack
Knowing what a data processing agreement is and what it should contain is the easy part. The real challenge? Making sure those agreements are actually in place and being followed across your entire, sprawling tech stack.
Putting a DPA into action isn’t just a legal checkbox. It’s a hands-on process of auditing, onboarding, and continuous validation that connects your legal promises to your technical reality. This isn’t a one-and-done task; it’s an ongoing discipline.
First things first: you need a complete map of your existing vendors. You have to figure out every single tool that touches personal data and confirm whether a signed DPA is already in place. For most companies, this exercise is an eye-opener, revealing surprising gaps where agreements are missing, outdated, or were never actually signed.
It's a heavy lift, no doubt, but it's completely non-negotiable. The goal is to create a central inventory of all your data processors and the status of each DPA. This gives you a clear snapshot of your compliance health and a straightforward roadmap to fix what’s broken.
Auditing Your Current Vendor Stack
Start by sorting your vendors based on the kind of data they handle. A payment processor that sees financial information needs a much closer look than a simple scheduling tool. The idea is to find and focus on your highest-risk relationships first.
Your audit checklist should cover these key actions:
- Inventory All Processors: Build a master list of every third-party service that processes user data. Think analytics platforms, marketing automation tools, cloud hosts, and customer support software.
- Locate Existing DPAs: Dig up the current DPA for each vendor. Double-check that it’s been properly signed and executed by both sides.
- Review for Modern Compliance: Old DPAs can be a liability. Scrutinize any agreement signed before recent regulations to ensure it aligns with current laws like GDPR and CCPA. A DPA from 2017 probably won't cut it today.
- Identify and Close Gaps: If a DPA is missing, get the process started to sign one immediately. If an existing one is weak, reach out to the vendor to discuss an updated addendum.
This audit creates your baseline—a single source of truth for vendor compliance. It’s the foundation for building a much smarter, more proactive implementation strategy.
Embedding DPAs into Your Procurement Process
Once your existing stack is buttoned up, you need to stop new gaps from appearing. The simplest way to do this is to bake DPA reviews directly into your procurement process for any new software.
Your new mantra should be: "no DPA, no deal."
Before you sign a contract for that shiny new martech or analytics tool, your legal and data teams need to review the vendor’s DPA. This has to happen before you agree on commercial terms, not as a last-minute scramble. Waiting until the end creates pressure to accept weak terms just to get the tool live.
A Data Processing Agreement should be treated as a core part of the vendor evaluation, just like pricing or features. A vendor's refusal to sign a robust DPA is a significant red flag about their commitment to data privacy and security.
Validating Compliance with Automated Observability
Signing a DPA is a critical legal step, but let’s be honest—it doesn’t guarantee the vendor’s tech will actually behave as promised. A contract can say a vendor won't collect PII, but a simple misconfiguration or a bug on their end could make it happen anyway. This is where automated observability is no longer a nice-to-have.
Automated analytics QA and observability platforms act as your eyes and ears, continuously monitoring the data flowing to your vendors in real time. They can automatically flag violations that would otherwise fly completely under the radar, like:
- Rogue Data Collection: Spotting when a vendor starts collecting data points that aren't specified in the DPA.
- Unexpected PII Leaks: Alerting you if sensitive information like emails or names is being sent to a tool that should never receive it.
- Cross-Border Data Transfer Issues: Validating that data is being sent to the geographic regions you agreed upon in the contract.
This kind of continuous validation transforms your DPA from a static document collecting dust into a living, enforceable agreement. By bridging the gap between legal terms and technical reality, you can catch and fix compliance issues before they turn into major incidents.
For example, teams can maintain data privacy compliance in Tealium by using automated tools that ensure their tag management system sticks to the letter of their DPA guidelines. It’s a proactive approach that closes the loop and makes sure the promises made in your DPAs are actually kept.
Navigating Sub-Processors and International Data Transfers
Getting a signed data process agreement is a major win, but the work doesn't end there. Today’s tech stacks are tangled ecosystems where data rarely stays in one place. It flows from your primary vendor to their vendors, creating a long chain of third parties.
This section tackles two of the thorniest parts of any DPA: keeping tabs on your vendor's vendors (sub-processors) and handling the complexities of international data transfers.
Untangling the Web of Sub-Processors
Think of your main vendor as a general contractor you hired to build a house. You have a solid contract with them, but they’ll bring in subcontractors—plumbers, electricians, painters—to do the actual work. In the data world, those subcontractors are called sub-processors.
A sub-processor is any other company your primary vendor uses to process your data. This could be a cloud host like Amazon Web Services or a support tool like Zendesk. The tricky part? You’re still on the hook for what happens to your data, so you need visibility and control over that entire supply chain.
The core idea here is accountability. Your vendor can't just hand off your data to another company without your say-so. A well-drafted DPA gives you that oversight.
Here’s what to look for:
- Prior Authorization: The vendor must get your written consent before they bring on a new sub-processor. No surprises.
- Sub-Processor List: They need to maintain and share an up-to-date list of every sub-processor touching your data.
- Back-to-Back Obligations: Your vendor is required to have a DPA with each of their sub-processors that mirrors the same protections you have with them. This creates a cascade of security down the line.
Without these controls, your data could end up with some unknown fourth or fifth party that has flimsy security, creating a massive compliance blind spot.
A vendor's sub-processor list isn't just a formality; it's a map of your data's journey. Scrutinizing this list is critical to understanding your full exposure and ensuring every link in the chain is secure and compliant.
Putting a DPA into practice involves a few key stages, from auditing your current vendors to validating that they're sticking to the agreement.
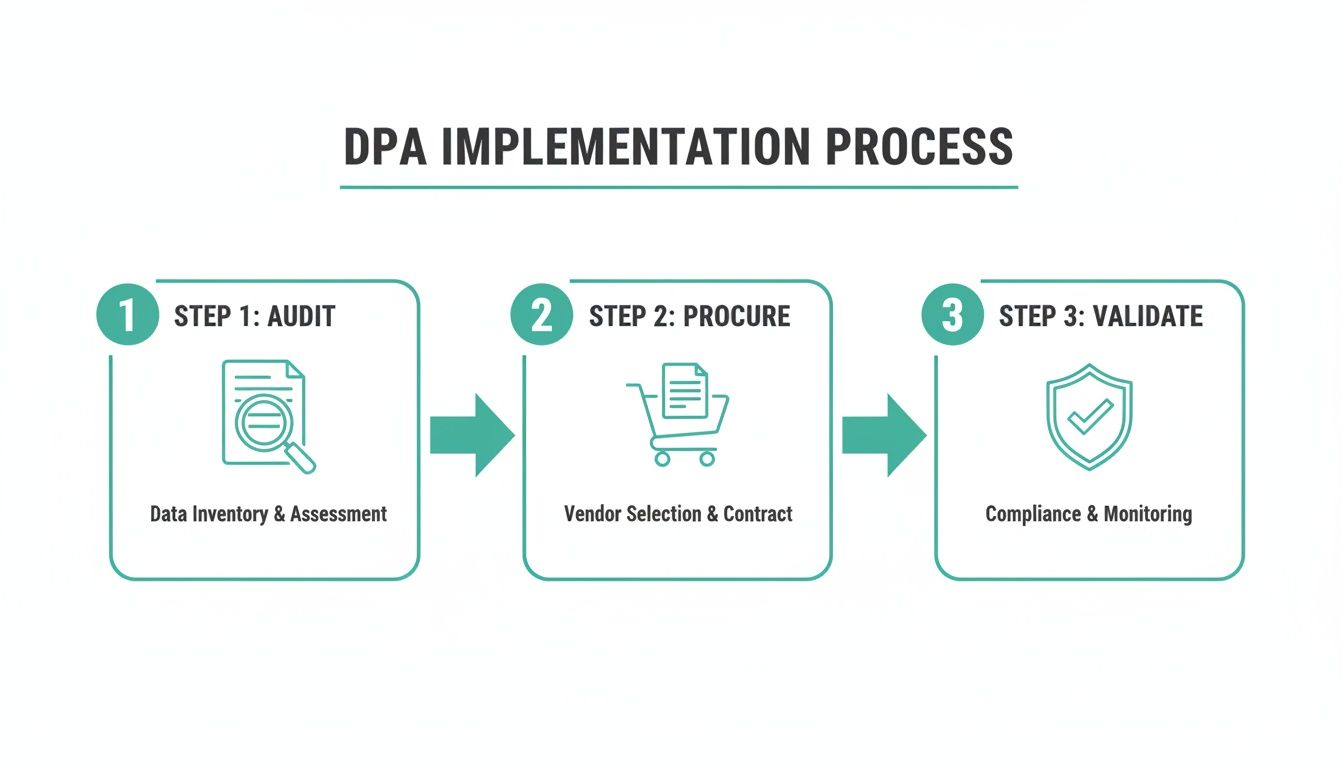
This workflow shows the essentials: audit what you have, make DPAs a non-negotiable part of procurement, and continuously validate that data is being handled exactly as the contract says.
Crossing Borders: International Data Transfers
Things get even more complicated when your data crosses international borders, especially if it’s coming from a place with strict privacy laws like the European Union. Moving EU data to a country like the United States isn't as simple as flipping a switch; it requires specific legal safeguards to ensure that data remains protected.
A simple question like "where are your servers located?" can quickly reveal just how critical this is.
The go-to mechanism for this has long been Standard Contractual Clauses (SCCs). These are pre-approved legal templates from the European Commission that both parties sign to guarantee adequate data protection. However, after the pivotal Schrems II court ruling, just signing SCCs isn't enough anymore.
Now, companies must also complete a Transfer Impact Assessment (TIA). A TIA is basically a risk assessment to confirm that the laws in the destination country—like government surveillance programs—don’t override the protections promised in the SCCs.
This is a moving target. For instance, the EU’s updated SCCs forced vendors to get matching agreements from their own sub-vendors, sending ripples through global supply chains. More recently, Switzerland's tough new Federal Act on Data Protection (FADP) also requires DPAs. As privacy frameworks evolve, having a solid DPA process is the only way for teams to maintain security and compliance across borders.
Common Questions About Data Processing Agreements
Once you get the hang of the basics, a whole new set of practical questions pop up the minute you start dealing with a data process agreement in the wild. This section cuts through the noise to tackle the most common things that trip up marketers, data teams, and business owners.
Think of it as your go-to cheat sheet for the everyday hurdles of managing DPAs and vendor relationships.
Who Is Responsible for Providing the DPA?
This is a classic point of confusion, but the answer is usually pretty simple. In most cases, the data processor—that is, your vendor or service provider—will hand over their standard DPA for you to review and sign.
It just makes sense. An analytics platform might have thousands of customers, and it's far more efficient for them to create a standardized agreement that reflects their internal data practices than to hash out a unique DPA with every client.
But don't mistake "standard" for "non-negotiable." As the data controller, the buck stops with you when it comes to protecting user data. It's your job to comb through that vendor DPA and make sure it ticks all your legal and security boxes. If you spot gaps or clauses that make you nervous, you absolutely have the right—and the responsibility—to push for changes.
Can a DPA Be Part of the Main Service Agreement?
Yes, and it happens all the time. It's very common to see a DPA incorporated into a bigger contract like a Master Service Agreement (MSA) or Terms of Service, usually as an addendum or exhibit.
For instance, the main agreement might include a line that says something like, "The parties agree to comply with the terms of the Data Processing Addendum, attached as Exhibit A and incorporated herein by reference."
This is a perfectly sound legal approach that keeps all the contractual pieces in one place. The trick is to make sure the DPA is explicitly named and legally tied to the main contract. A fuzzy mention of "data protection" isn't enough. You need a specific, binding DPA, whether it's a separate document or a formal part of a larger agreement.
Do We Need a DPA for Every Single Vendor?
The short answer is yes—if that vendor processes personal data on your behalf. This isn't just about the big-name platforms handling massive datasets.
Think about all the tools you use daily. A DPA is non-negotiable for:
- Email Marketing Services: They’re processing your customer email lists.
- Cloud Hosting Providers: They store your application and all the user data that comes with it.
- Customer Support Software: They manage support tickets loaded with personal information.
- Analytics and Martech Tools: They process user behavior, IP addresses, and other identifiers.
- Payroll or HR Software: They handle some of the most sensitive employee data you have.
The litmus test isn't the vendor's size or how much data they touch. It’s the act of processing personal data. If a third party is handling information that can identify a real person based on your instructions, regulations like GDPR require a DPA. Since 2018, GDPR alone has resulted in 2,248 fines totaling nearly €6.6 billion, a stark reminder of the financial risks of getting this wrong.
What Happens If a Vendor Refuses to Sign a DPA?
A vendor refusing to sign a solid DPA should set off alarm bells. In today's privacy-focused world, any legitimate data processor should understand that these agreements are just part of doing business.
If you get pushback, it could signal a few things, none of them good:
- Their internal data practices might not be up to snuff with current laws.
- They may not have the security infrastructure needed to protect your data.
- They might not even understand their legal duties as a data processor.
If a vendor won’t sign a Data Processing Agreement, you should seriously question whether you want them handling your data. Partnering with a non-compliant processor shifts a massive amount of risk onto your company, opening you up to serious legal and financial trouble.
Honestly, the best move is to walk away. Find a provider who takes data protection as seriously as you do. The risk of working with a vendor without a DPA is just too high to justify.
A signed DPA is a huge step, but it’s not a silver bullet for compliance. A simple misconfiguration can still cause a data leak or violate the terms you just agreed to. Trackingplan offers automated observability to ensure your vendors' real-world data processing lines up perfectly with your DPA. It alerts you in real time to rogue data collection, PII leaks, and other critical gaps. Discover how to bridge the gap between your legal agreements and technical reality.