Privacy and compliance aren't just buzzwords in digital analytics; they represent the set of rules and best practices for collecting, using, and storing user data both ethically and legally. This is no longer a task for the IT department to handle in the background. It's now a core business strategy, absolutely essential for building trust and avoiding massive financial penalties.
The New Rules of Digital Analytics and Data Privacy
Welcome to the new reality of digital analytics, where privacy isn't just a feature—it's the entire foundation. For years, companies gathered huge amounts of user data with very few restrictions, but that free-for-all is officially over. Today, a proactive approach to privacy and compliance is mission-critical for any organization hoping to build a sustainable, trustworthy brand.

Think of your data collection like a digital supply chain. Every single piece of information, from a simple click to a complex user journey, has to be ethically sourced, securely handled, and used transparently. This isn't just a trend; it's a major shift driven by both consumer expectations and a growing web of global regulations.
The Rising Stakes of Non-Compliance
The risks of sloppy data practices are more real than ever. We're not talking about small fines or a slap on the wrist anymore. We're talking about serious financial and reputational damage.
This regulatory web is only getting tighter and more complex. By early 2025, the number of countries with their own data and consumer privacy laws reached 144. This global expansion, kicked off by landmark regulations like GDPR, means analytics platforms have to stay compliant across borders. They need to spot PII leaks or consent misconfigurations in real-time to dodge severe penalties, which have already totaled €7.1 billion in GDPR fines alone since 2018. You can find more stats on this trend over at Usercentrics.com.
The biggest risk isn't just the one-time fine. It’s the permanent loss of customer trust. Once users believe you've mishandled their data, winning back their loyalty is an uphill battle that many companies never win.
Compliance as a Strategic Advantage
While the penalties are certainly scary, looking at compliance as just another chore is a huge missed opportunity. If you frame it as a strategic advantage, you can build a more resilient business and earn deeper loyalty from users in this privacy-first world. When people trust that you respect their data, they’re far more likely to engage with your brand.
A solid privacy framework sends a clear message: you value your customers for more than just their wallets. It’s a commitment to ethical practices that can set you apart from the competition. Key benefits include:
- Enhanced Customer Trust: Being transparent about how you use data builds confidence and makes customer relationships stronger.
- Improved Data Quality: When you focus on collecting only necessary data with clear consent, you often end up with more accurate and valuable insights.
- Future-Proofing Your Business: A strong compliance posture gets your organization ready for whatever new regulations and market shifts are coming next.
Ultimately, mastering privacy and compliance isn't about limiting your analytics. It's about making them smarter, safer, and more sustainable. A crucial first step is understanding consent, which you can learn all about in our guide on what is consent management.
Understanding the Core Concepts of Data Privacy
Diving into the world of data privacy can feel like you're learning a whole new language. To build a solid, compliant analytics foundation, you first need to get a handle on the key terms that define the rules of the game. This isn’t just about checking off boxes on a compliance sheet; it's about fundamentally shifting how you think about and manage user information.
PII: The Digital Fingerprint
At the very center of every privacy regulation is the concept of Personally Identifiable Information (PII). The easiest way to think about PII is as a person's digital fingerprint—any piece of data that can be used on its own, or combined with other data, to identify, contact, or locate a specific individual.
This obviously includes things like names, email addresses, and phone numbers. But it also covers less direct data points that can still pinpoint someone, like IP addresses, device IDs, or even hyper-specific geolocation data.
On the other hand, you have anonymized data, which is more like a shadow. It lets you see the broad shapes and patterns of user behavior without revealing who is casting it. A truly compliant analytics strategy aims to work with these shadows as much as possible, gathering rich insights without collecting sensitive digital fingerprints.
Consent: The Handshake Agreement
Consent is simply the permission users give you to collect and process their data. But not all consent is created equal, and knowing the difference is absolutely critical for staying compliant.
- Explicit Consent: This is the gold standard. It's a clear, direct "yes" from the user—they actively check a box (that wasn't pre-checked) or click an "I Agree" button after you’ve given them clear information. Think of it as a firm handshake where both sides know exactly what they're agreeing to.
- Implicit Consent: This is more of an assumption based on a user's actions, like if they keep scrolling on your site after seeing a cookie banner. Most modern laws, especially GDPR, see this as flimsy ground for collecting non-essential data. It’s more of a guess than a true agreement.
A core principle of modern privacy law is that consent must be freely given, specific, informed, and unambiguous. Relying on implicit consent is like building a house on a shaky foundation—it’s bound to cause problems down the line.
Data Minimization: Collecting Only What You Need
The principle of data minimization is as simple as it is powerful: you should only collect the data that is absolutely necessary to achieve a specific, stated goal. It’s a direct challenge to the old mindset of hoarding as much data as possible "just in case."
For instance, if your goal is to figure out which blog posts are the most popular, you only need to track page views and anonymized user IDs. You have no business collecting the reader's name, email, or exact location for that purpose.
This principle instills discipline. By forcing you to define the "why" behind every single data point you collect, you not only slash your compliance risk but also sharpen the quality of your analytics. A focused, clean dataset is almost always more valuable than a massive, noisy one.
Spotting PII in Unexpected Places
One of the sneakiest compliance challenges is that PII has a habit of leaking into your analytics from places you'd never expect. It’s not always as clean-cut as a user_email field. Teams need to be on high alert to prevent accidental data collection from sources like these:
- URL Query Parameters: After someone fills out a form, their email or name can get slapped right into the URL string (e.g.,
[email protected]). Since most analytics tools grab the full URL by default, you’ve got an instant PII breach on your hands. - Event Properties: A well-meaning developer might accidentally include a sensitive user ID or a full name within the properties of a custom event like
purchase_completed, completely unaware of the compliance fallout. - Third-Party Scripts: Marketing and advertising tags can sometimes scrape data from your site in ways you don’t control or even know about, leading to data being shared with vendors without your explicit intent.
Getting these foundational concepts right is the first real step toward building an analytics implementation that’s compliant by design. It moves you from a reactive mode of constantly cleaning up messes to a proactive one of preventing them, ensuring user trust is always at the heart of your data strategy.
Putting Privacy Principles into Practice
Knowing the core concepts of data privacy is one thing. Actually applying them to a tangled web of analytics tools, tags, and tracking scripts? That's a whole different ballgame. This is where theory hits the pavement, moving from just knowing the rules to building a system where privacy and compliance are baked in from the start.
The real goal isn't just to react to privacy laws but to get ahead of them. It's about orchestrating how consent is managed, how data is scrubbed clean of sensitive info, and how long you hold onto it. When you get this right, compliance stops feeling like a frantic, manual checklist and becomes an automated, reliable part of your analytics engine.
Consent Management as Your First Line of Defense
Think of a Consent Management Platform (CMP) as the bouncer at the door of your data collection club. Its main job is to respect a user's choice, deciding which analytics and marketing tags get past the velvet rope and which ones have to wait outside. Just slapping a cookie banner on your site doesn't cut it; that banner has to be wired correctly to stop data from being sent before a user explicitly says "yes."
Picture your website's tags as a fleet of delivery trucks, each ready to haul data off to different places like Google Analytics, a CRM, or an ad platform. The CMP is the dispatcher. It only gives a truck the green light after getting clear permission from the user for that specific delivery.
A classic mistake we see all the time is tags firing the second a page loads, long before the CMP has a chance to even ask for consent. This is a direct violation of most privacy laws and usually stems from a misconfigured tag manager. A solid setup makes sure that consent signals are the very first thing the system checks, making every other tag conditional on that initial thumbs-up.
This diagram shows the ideal flow for handling user data, ensuring you’re staying private and compliant from beginning to end.
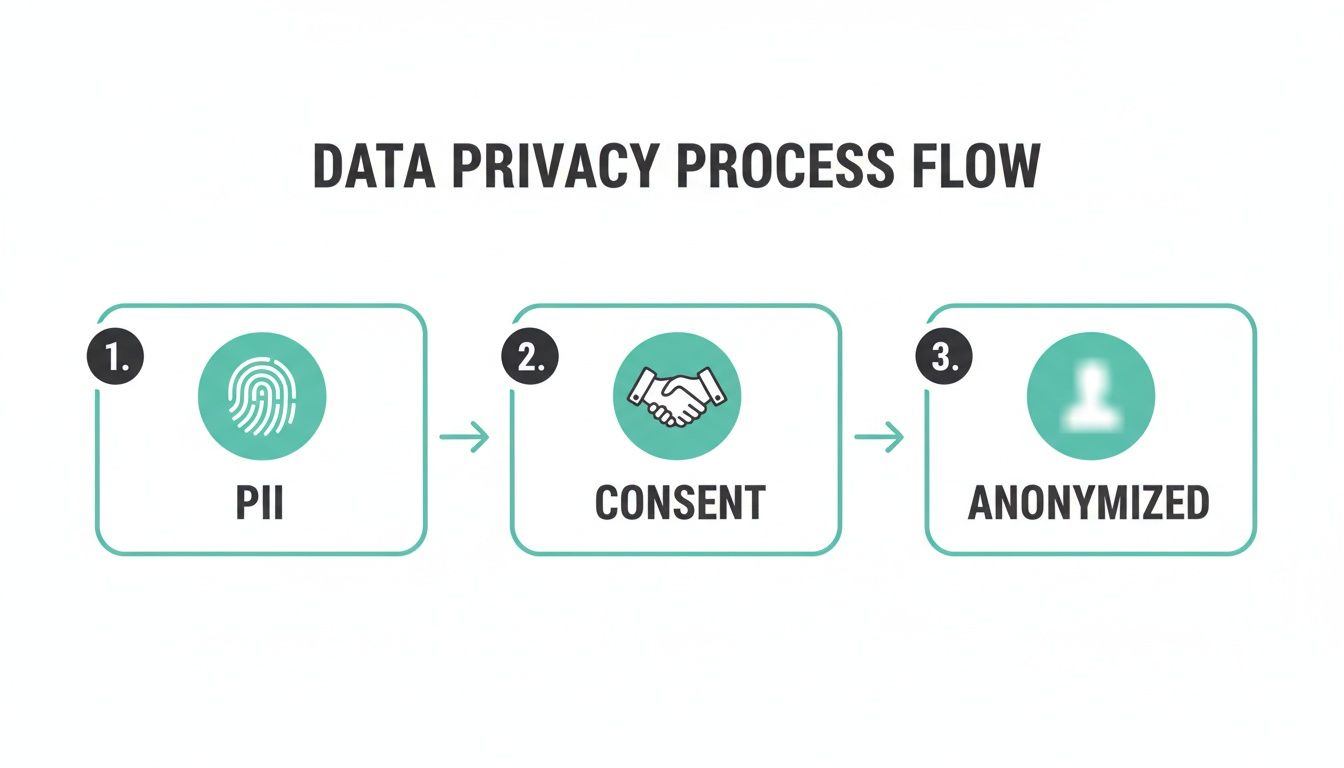
The flow here is critical: spot potential PII, get user consent, and then—and only then—process the anonymized data. That's how you build privacy right into the workflow.
Proactive PII Sanitization Techniques
Even with a perfect consent setup, PII has a nasty habit of slipping through the cracks. Accidental data leaks are one of the most common—and riskiest—compliance headaches. Proactive sanitization means building in automated checks that strip out sensitive information before it ever leaves the user's browser.
The smartest privacy strategy works on the assumption that human error is a given. When you build automated safeguards to catch and remove PII in real-time, you create a system that’s resilient by design, not just by policy.
Here are a few common traps and how to sidestep them:
- URL Scrubbing: PII loves to hide in URL query parameters, especially after someone fills out a form (like
[email protected]). You can use JavaScript or built-in functions in tools like Google Tag Manager to parse the URL and either remove or hash any sensitive parameters before the data gets passed to your analytics tags. - Form Submission Leaks: Shady third-party scripts, especially for session recording or ads, can sometimes grab every single keystroke from your forms. You can block this by implementing strict Content Security Policies (CSPs) and being extremely picky about the third-party vendors you work with.
- Event Property Auditing: It's easy for a developer to accidentally push an email address or a name into a custom event property. A strong governance process, backed by a crystal-clear tracking plan, ensures every single property is reviewed for privacy red flags before it ever makes it to production. We talk a lot more about embedding these concepts in our article on privacy by design principles.
Establishing Sensible Data Retention Policies
The principle of data minimization isn’t just about what you collect; it’s also about how long you keep it. Hoarding user-level data forever is just asking for trouble. If you ever have a data breach, the damage is way worse if you’re sitting on years of historical user data instead of just a few months.
Every single analytics and marketing tool you use needs its data retention settings configured on purpose, not by default. Here's a practical way to tackle it:
- Map Your Tools: Make a list of every platform that collects user data (Google Analytics, Amplitude, Mixpanel, your CRM, etc.).
- Define Your Needs: For each tool, ask yourself: what’s the maximum lookback period we genuinely need for analysis? Do you really need user-level data from three years ago, or would 14 months do the trick?
- Configure the Settings: Go into the admin settings for each tool and set the data retention period to match your needs. For instance, in Google Analytics 4, you can set event data retention to either 2 months or 14 months.
When organizations get serious about putting privacy principles into practice, they formalize these commitments in a comprehensive Privacy Policy. This document is more than just a legal box to check. It's a public promise about how you handle data, including your retention policies, which builds transparency and trust. By making sure your technical settings align with your public promises, you create a consistent and defensible approach to privacy.
Building Your Data Governance and Auditing Framework
Setting up a compliant analytics system isn't a "set it and forget it" task. What gets a green light today can quietly become a major liability tomorrow if you're not paying attention. A solid data governance and auditing framework is the only way to maintain privacy and compliance as your business, your team, and your tech stack all grow and change. This is how you move from stressful, last-minute fire drills to a calm, managed, and automated process.
The Tracking Plan: Your Single Source of Truth
At the core of any good governance model is a tracking plan. Think of it as the constitution for all your data collection—a living document that clearly defines every event, property, and user attribute you collect, along with its specific business purpose. This plan becomes the single source of truth that gets developers, marketers, and analysts on the same page about what data is approved and why.
Without this central document, teams end up working in silos. A marketer might ask a developer to add a quick event without thinking through the privacy side, accidentally leading to PII collection. A tracking plan forces those critical conversations to happen before any code is written.
A well-maintained tracking plan transforms data collection from an ambiguous free-for-all into a deliberate, accountable process. It's the bedrock of preventing unauthorized data from ever entering your systems.
By making it a rule that any new tracking must first be defined and approved in the plan, you create a powerful gatekeeping mechanism. This ensures every single piece of data has a clear owner and a legitimate business reason for being there, which lines up perfectly with the principle of data minimization.
Moving Beyond Manual Spot Checks
For a long time, auditing analytics for compliance issues meant tedious, manual spot-checks. An analyst or developer would pop open their browser's dev tools, inspect a few network requests on key pages, and hope to catch any rogue data. This approach just doesn't cut it anymore—it's fundamentally flawed.
Manual audits are:
- Slow and Resource-Intensive: They eat up a ton of time from skilled team members who have bigger things to worry about.
- Incomplete: Spot-checks only cover a tiny fraction of user paths, devices, and scenarios. It's incredibly easy to miss intermittent or edge-case PII leaks.
- Reactive, Not Proactive: By the time a manual check finds a problem, that non-compliant data has likely been flowing into your systems for weeks or even months.
Relying on this outdated method is like hiring a security guard who only patrols one hallway for five minutes a day. You might get lucky, but you’re leaving the rest of the building wide open.
The Power of Automated Observability
The only solution that truly scales is shifting from periodic manual checks to continuous, automated observability. An analytics observability platform acts like a 24/7 watchdog for your data, automatically monitoring every single event sent from your websites and apps in real time.
This automated system constantly compares all incoming data against your official tracking plan, instantly flagging anything that looks out of place. Think of it as a vigilant, automated QA engineer that never sleeps. It can immediately detect critical privacy and compliance threats that manual checks would almost certainly miss:
- Rogue Events: Unplanned events snuck in by developers that aren't defined in your tracking plan.
- Unexpected PII: Sensitive data like emails or names showing up in properties where they absolutely do not belong.
- Schema Deviations: Events that don't match the structure you laid out in your governance plan.
When building out a robust governance and auditing framework, integrating specialized tools is a must. For example, solutions offering GDPR compliant HR software with Microsoft Purview Integration can help manage sensitive employee data within your broader governance strategy. This just goes to show how important it is to use technology to enforce your policies consistently across every part of the business.
By putting automated monitoring in place, you turn governance from a painful, periodic audit into a constant, automated state of readiness. It gives you the peace of mind that your data collection stays aligned with your privacy commitments, every minute of every day.
How Automated Observability Prevents Privacy Breaches
Manual audits and periodic spot-checks just don’t cut it anymore for managing the complex web of privacy and compliance. In today’s fast-paced development cycles, human error isn't just a possibility; it's an inevitability. This is where automated observability platforms step in, acting as an essential, always-on defense mechanism. They turn your data governance framework from a static document into a dynamic, active shield.
These systems work by continuously monitoring 100% of your analytics traffic against your predefined tracking plan and privacy rules. Instead of waiting for a quarterly audit to hopefully stumble upon a problem, you get instant alerts the moment something deviates from the plan. This real-time detection is the only truly scalable defense against the common, high-risk scenarios that lead to costly breaches.

Scenario One: The Accidental PII Leak
Picture this: a developer is rushing to deploy a new feature for your e-commerce site. In a quick code push, they accidentally include the customer's email address within the purchase_completed event. Just like that, this single mistake is now sending sensitive PII to every single analytics and marketing tool that listens for this event, creating a massive compliance violation.
A manual audit might not catch this for weeks, if ever. By then, thousands of customer emails could have been improperly processed and stored across various third-party vendors.
Automated Observability in Action: An observability platform like Trackingplan would spot this anomaly instantly. Because the tracking plan explicitly states the
purchase_completedevent should never contain an
Scenario Two: The Rogue Marketing Tag
Your marketing team wants to test out a new retargeting vendor, so they add the vendor’s JavaScript tag through Google Tag Manager. The problem? They misconfigure the firing trigger, causing the tag to load on all pages, completely ignoring the user’s consent status. This new script is now collecting user interaction data before anyone has a chance to opt-in, blowing a hole right through your carefully configured CMP.
This is a serious breach of regulations like GDPR and CCPA. The tag is essentially a black box, sending data to a third party without permission or oversight and exposing your business to significant legal risk. These kinds of misconfigurations are a leading cause of consent-related fines, which can easily climb into the millions of dollars.
This screenshot shows an example of how Trackingplan’s real-time alerts can immediately flag critical PII leaks.

The alert clearly identifies that PII has been detected, providing the context needed for immediate action and remediation.
Scenario Three: The Third-Party Data Scraper
Plenty of websites use third-party scripts for things like chatbots, session replay tools, or A/B testing. But what happens when one of those vendors pushes an update to their script—without your knowledge—and it starts scraping data from form fields on your checkout page? All of a sudden, sensitive inputs like names, addresses, or even payment details are being collected by a script you don't control.
This is a nightmare scenario for any data privacy officer. It’s a total loss of control over your users' most sensitive information, creating a massive security vulnerability and a direct violation of your own privacy policy.
- How Automation Stops It: A proper observability tool doesn’t just watch your own analytics; it monitors all network traffic. It can be configured to detect when third-party scripts are grabbing data from sensitive DOM elements, like form input fields.
- The Instant Alert: The second the script starts this unauthorized collection, an alert is triggered. Your security and dev teams get a precise report detailing which script is the culprit and what data it's capturing.
- Rapid Resolution: Armed with this information, your team can block the script or contact the vendor to fix it immediately, containing the breach before it impacts a large number of users.
In each of these very real scenarios, automation provides the speed and scale that manual processes simply can't match. It transforms your approach to privacy and compliance from a reactive, cross-your-fingers strategy into a proactive, continuously enforced system that protects both your users and your bottom line.
Frequently Asked Questions About Analytics Privacy
Let's be honest: navigating the finer points of privacy and compliance can feel like walking through a minefield. As teams hustle to bring their analytics up to modern standards, the same practical questions and sticking points tend to crop up. Here are some clear, straightforward answers to the questions we hear most often from developers, marketers, and analysts in the trenches.
What Is the Most Common Way PII Is Accidentally Leaked?
By far, the most common culprit for accidental PII leaks is the URL query parameter. It happens all the time: a user clicks a link from an email campaign or submits a form, and suddenly their email address or name is sitting right there in the URL. If that URL isn't properly scrubbed, your analytics tools will happily slurp it up and pass it along to your vendors, landing you in hot water.
Another classic mistake is when developers, often in a rush to ship a new feature, accidentally embed PII into custom event properties or the dataLayer. It’s an easy oversight when speed is the priority, but the compliance fallout can be huge.
Can I Still Perform User-Level Analysis and Remain Compliant?
Yes, absolutely. You don’t have to give up powerful user-level analysis. The trick is to stop using direct PII and start using pseudo-anonymous identifiers.
Instead of tracking a user by their email, you assign them a unique, randomly generated user ID (like a UUID). This ID is meaningless to the outside world and can't be traced back to an individual without access to your secure internal database. It allows you to track journeys and build cohorts just as effectively, but in a way that fully respects privacy. Modern analytics platforms are built to work this way, using these anonymous IDs as the foundation for user profiles.
How Does Automated Monitoring Differ from Manual Analytics Audits?
Think of it like this: a manual audit is like a security guard who does a quick walkthrough once a month, while automated monitoring is a 24/7 security camera system watching every corner.
- Manual Audits: These are periodic, incredibly slow, and full of blind spots. An analyst might spend days combing through network requests for a tiny sample of user sessions, completely missing issues that only pop up on certain devices or at odd hours.
- Automated Monitoring: A platform like Trackingplan watches 100% of your analytics traffic around the clock. It automatically checks every single event against your tracking plan and privacy rules in real-time.
Automated monitoring finds problems in minutes that a manual audit might not find for months, if at all. It turns governance from a reactive, once-in-a-while chore into a proactive, always-on process.
What Is Data Minimization and How Do I Apply It?
Data minimization is a core privacy principle that basically says: only collect what you absolutely need for a specific, legitimate purpose. It’s the polar opposite of the old "hoard all the data just in case" mindset.
Putting it into practice means auditing every event and property you collect. For each one, you have to ask the tough question: "What specific business decision does this data enable?" If you can’t give a clear, compelling answer, it’s probably time to get rid of it.
Your best weapon here is a well-defined tracking plan. It acts as the blueprint, explicitly stating what data to collect and why, preventing junk data from ever being tracked in the first place. This disciplined approach not only boosts your privacy and compliance but also dramatically improves the quality of the data you do collect.
Ready to move from reactive audits to proactive protection? Trackingplan provides the automated observability you need to detect PII leaks, consent misconfigurations, and other critical compliance issues in real time. Stop guessing and start governing your analytics data with confidence.








